OMFG, BREAKING NEWS: Thousands of WordPress sites affected by some vulnerability.
Yeah … Saw another one of those today. This time it was this one:
Keylogger found on thousands of WordPress-based sites, stealing every keypress as you type
I’m not sure if this even serves as clickbait. But I clicked the link. Some 2,000 sites are affected by malware that collects login credentials and use JS to mine cryptocurrency.
Yawn …
Some perspective may be needed here:
WordPress is quite a chunk of the web
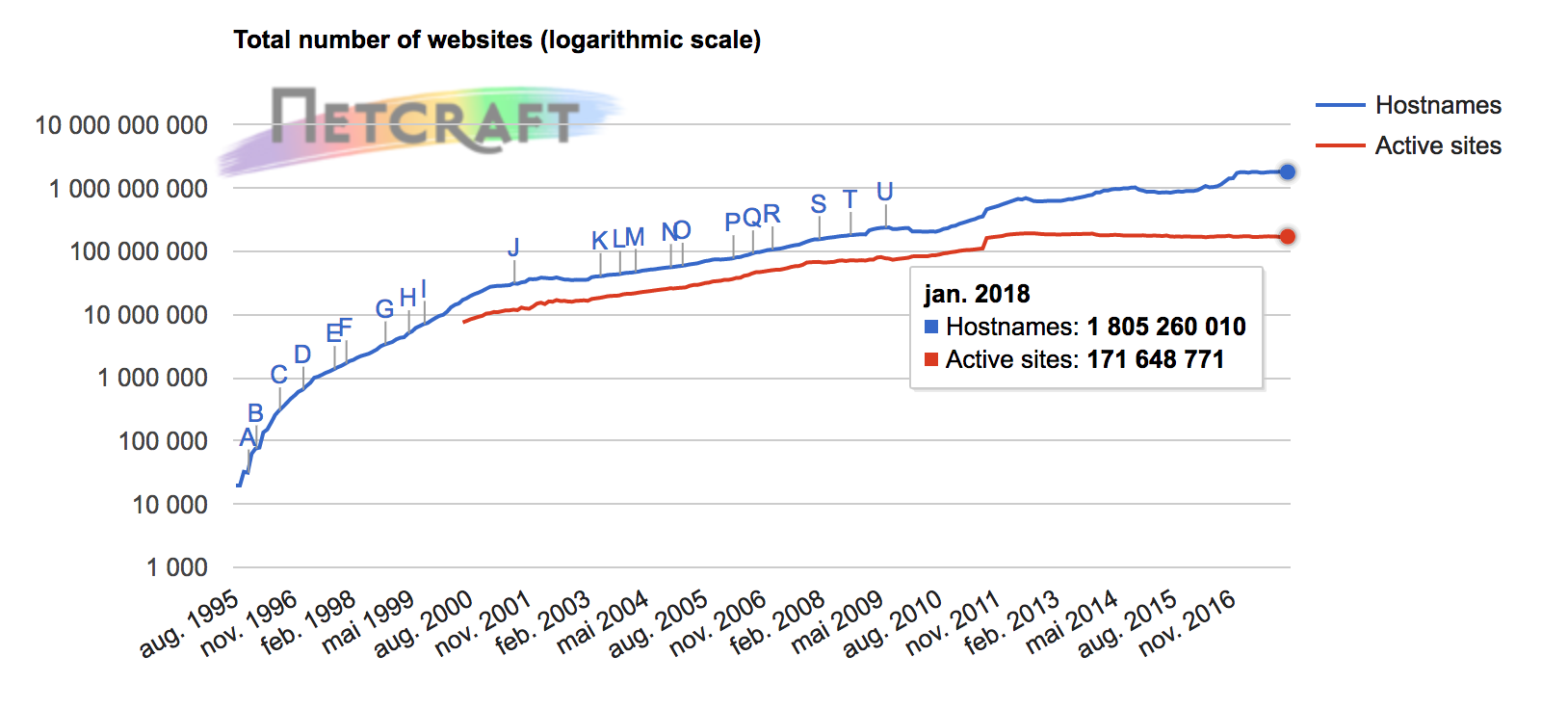
In the January 2018 survey, Netcraft received responses from 1,805,260,010 sites across 213,053,157 unique domain names and 7,228,005 web-facing computers. Of all of these, Netcraft estimates that 171,648,771 sites are active sites.
According to w3tech, WordPress powers 29.3% of all websites.Yes, almost 3 out of 10 of all websites.
Extrapolate those numbers and you’ll see that there are more that 50,000,000 websites running WordPress. Oh, btw: Sites like wordpress.com, which runs tens of millions of WordPress-powered sites, are only counted once.
So if 2,000 of those 50,000,000 sites (again: sites like wordpress.com with tens of millions sites are counted once!) are compromised, that’s less than 0.004% of all WordPress sites. If you look at the dumb numbers, there’s actually a 75% higher chance of you dying in a car accident than having your WordPress website compromised.
But we are going to look beyond the dumb numbers. Because one of WordPress’ greatest strengths is its extensibility. I’ve never heard of anyone actually running a WordPress website without any extensions. On wordpress.org alone, there are ~54.000 third party plugins available.
Now, 0.004% of all WordPress sites, means 0.001% sites on the internet if we use Netcraft and w3techs numbers. So because of some “WordPress vulnerability” 0.001% sites on the internet was compromised. Well … but … What about the 29.3% of the other sites on the internet running WordPress, where the 0.001% sites are regarded a rounding error? If there’s a security issue in WordPress, Why aren’t 3 out of 10 sites on the internet compromised? Maybe the issue isn’t with WordPress at all after all?
The world’s second most popular CMS is Joomla!, which runs 3.2% of all websites. Compare that with the Netcraft active sites numbers, and you get that about 5.5 million sites run Joomla!. That’s roughly the same amount of WordPress sites that have installed the Yoast SEO plugin. One single plugin. There are likely more WordPress plugins activated at any time than there are websites on the internet.
Is it really a WordPress security issue?
There is probably as much, or more, diversity within the WordPress segment of the world wide web, as there is between the Content Management Systems on it. WordPress is a bigger part of the internet than many other popular technologies ever was: Flash, Director, VBScript, JScript, ASP, ColdFusion etc. It has a bigger piece of the World Wide Web than what CSS had when I started using it. It will soon become, if it isn’t already, one of the technologies we count as the big pieces that make up the web.
Now, if there’s a vulnerability in jQuery or React: Would you write an article about how x JavaScript sites are compromised without mentioning jQuery or React? It there’s a vulnerability in the Privacy Badger extension for Google Chrome, would you write an article about x Chrome users are compromised without even mentioning Privacy Badger? If Adobe Acrobat Reader has a vulnerability, would you write an article about x Windows users being compromised without mentioning Acrobat Reader at all?
These vulnerabilities have nothing to do with WordPress
- The software where they are found, are not affiliated with any of the developers on the WordPress development team.
- There is a WordPress security team, but they have no authority over 3rd party extensions.
- Plugins/extensions are developed by independent 3rd party developers, who have nothing to do with the central WordPress core development. And vice versa.
Then there are people who say that “WordPress is insecure (and yes, they know it’s the plugins), but the WordPress ecosystem facilitates it”. Well … Yes .… It is easy to make 3rd party extensions for WordPress. It is easy to install 3rd party extensions in WordPress. What do you want to change about that?
Users are users: Ignorant clickers
The reason WordPress sites get compromised is the same reason you have to reinstall your parents’ computer with 40 extension bars in Internet Explorer every holiday you visit. They have no filter whatsoever on what they click or what they install. How many times haven’t you heard “Nooo, I didn’t install that” and rolled your eyes?
There is a reason why companies put restrictions on employees’ computers and don’t let them install whatever. For marketing reasons, hosting companies will let you install whatever. Up until you install something stupid. If they’re a good hosting company, they will shut down your website (wut? read on!). If they’re a bad hosting company, they will let your site stay up, spreading spam, slowing down the other sites on the server and be a stepping stone to hack another site.
What can be done?
First of all: The way I see it, nothing actually has to be done. I’m doing just fine. I don’t install whatever, and I don’t use web hosts that let their users simply install whatever.
But in the long run, this “journalism” is negatively impacting the reputation of WordPress. The frustration over that is why I’m writing this post in the first place: it started as a comment on a “WordPress sites compromised” article (guess it grew out of that!).
The WordPress Foundation is defending the WordPress trademark, but there are still so many cases where a regular user can’t really distinguish between an “official plugin released by WordPress” (doesn’t exist, btw) and a 3rd party independent piece of software that builds upon WordPress in a totally unregulated way.
I’m not sure how to tackle this, but if you have an idea, please leave a comment or mention @bjornjohansen in a tweet.

Hey, Bjørn! Just came across your blog from the “www or not?” post, and it looks like this is gonna be a great resource for me, as I’m running a WordPress site now.
Good point. It’s super easy to just blame WordPress, when the underlying problem is a basic missing understanding of security. Challenge is that users are actually also the same type of people often hosting a WordPress installation, and as you say, they just “click away”. They will do whatever just to get the problem fixed, completely ignoring security.
It’s impressive how Apple has handled being so popular in terms of the iPhone vs. how little malware there has been, simply because they made the sandbox so limited.
I’m not sure the solution is people will get better.. I think they won’t. However, take how Facebook+Google and many others have really good security measures (ie. 2FA and warnings for warnings), and WordPress will probably go down that route. Why not enforce 2FA when logging into WordPress?
We previously used Joomla, but it was constantly hacked. Now we have no problem with wordpress.
your blog is very helpful for me